Security

Safety first
Protect your data with the
InPost Mobile application
General safety rules
Cyber-crime
These are all the issues that relate to Internet crime.
Phishing
This is one of the most common and popular methods of deception that cyber-criminals use. Phising consists in criminals impersonating a particular institution to obtain valuable and confidential information. These could be, for instance, passwords, logins, personal data, or bank account and credit card details.
One form of phising is the so-called SMS phising (smishing), which consists in sending text messages to induce the device user to take a specific action. Phishing messages always contain a link to a fake website, where an oblivious user provides criminals with their login and password.
Useful!
Phising attacks rely on emotions. The use of known social engineering techniques makes it very difficult to defend against such crimes. Watch out for attacks using the infamous 'friend method'.
- Never click suspicious links. Watch out especially for short links (like bit.ly) - hover your mouse over the link to check the actual website address.
- Do not open or reply to suspicious text messages. Doing so only provokes criminals to intensify attacks. Remember that you can always check the number in a search engine.
- Under no circumstances disclose your personal data. Apply the limited trust principle on the web. Do not even trust serious institutions if they ask you to update your data.
Spoofing
A method of internet fraud based on impersonation of a specific entity (a piece of software or another Internet user) in order to extort sensitive data, such as access to bank accounts. There are several types of spoofing: IP address spoofing, email spoofing, DMS spoofing, and caller information spoofing.
Spoofing is a relatively cheap operation that can be performed by anyone with basic IT knowledge. Own SMS gateway, fake domain, or use of technology give criminals almost unlimited possibilities of acting and extorting funds.
Useful!
On the website haveibeenpwned.com you can, by entering your email address, check if your data has leaked from other websites and is not in the possession of hackers. It is safe to use the site.
- Be careful when surfing the internet. Use an up-to-date browser, regularly clear your history, and check the links you click on.
- Do not reply to e-mails in which the sender asks you to provide private data, such as: address, social security number, or bank account number.
- Check email addresses and websites. If in doubt, contact the institution from which you have received this information directly and ask them to verify the message.
Malware
This is malicious software sent as an attachment, with the purpose of gaining access to your device. You should be especially careful about malware varieties such as: spyware, rootkits, Trojans, and keyloggers. Malware usually gets into your device via email. Therefore, under no circumstances should you download any attachments that you are not sure have come from an authentic and proven source.
Useful!
Malware gets into victims' devices most often via phising emails. An attachment to such an email contains a dangerous file, usually pretending to be a .zip or .doc file, but it can also be disguised as other files in a different formats.
- Never open or download attachments unless you are sure that they come from a verified source.
- Always check the sender's address, because criminals like to impersonate other companies
- Make sure to have verified, original anti-malware software.
Ransomware
A type of malware, which completely blocks access to the computer's operating system. Criminals usually demand a lot of money for unlocking the device. Ransomware can infect your computer via email or website, and the best specialists in such attacks not only encrypt the system, but also individual files and folders on your computer. This is why data backups are so important. Under no circumstances should the criminal's financial demands be met - the situation must be reported to law enforcement as soon as possible.
Useful!
The effects of a ransomware attacks are huge. The amounts demanded by hackers for unlocking access to the device reach thousands of dollars. A ransom demand for not disclosing the victim's private data is an increasingly popular form of this attack.
- Make sure your anti-virus software is always up-to-date and of good quality.
- Consider using a portable drive; if you lose access to your computer, you will be able to recover your data.
- Only visit trusted websites and do not open suspicious email attachments.
We recommend increased attention and caution in providing your data or "clicking"
suspicious messages. If you notice suspicious incidents, please report them to:
Learn about InPost security rules
Text messages
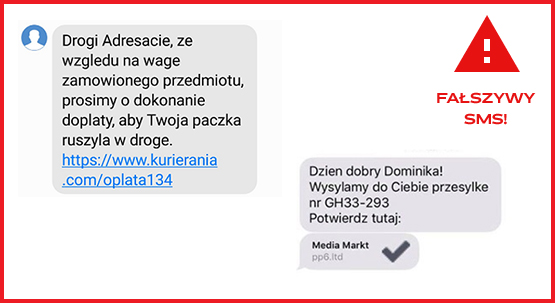
- Watch out for fake text messages.
Please be advised that InPost never sends text messages with information about surcharges. All billing information appears only in the Parcel Manager or on the invoice. - Watch out for messages that require you to send a paid SMS to "download shipment information"
Sending the text messages charges a fee that goes to the fraudsters' account. - If the message seems suspicious to you, check it at the source, i.e. the company that sent the message.
Call, write, or ask directly. Never dial the phone number provided in such an email or text message, and instead go to the website of the company that sent the text message or email and use the contact details provided on the website.
E-mail messages
- Make sure there is no typo in the email address.
Criminals send dangerous emails from fake but similar-sounding addresses, such as @intops.pl, @impost.pl or @inpost-eu.pl. E-mails sent by cyber-criminals differ from the originals mainly in spelling, strange, suspicious addresses and attachments. - Real InPost notification emails never contain any attachments!
If you receive a message with an attachment, under no circumstances open the file (usually with the extension .doc, .txt, or .pdf). In addition, the phrase list przewozowy ("waybill") often appears in the content of infected messages, which we never use. - Watch out for messages that require you to send a paid SMS to "download shipment information".
Sending the text messages charges a fee that goes to the fraudsters' account.

Applications
- Only download applications from a legal, authorized source.
Use common sense when using apps on your smartphone. You can download our InPost Mobile application (the best way to track shipments) - depending on the operating system you have - here:
Google Play App Store - Secure access to your applications.
Protect your phone with a password or PIN (but not something like 1234, 9876) or use a fingerprint lock. Secure your computer with a password, you can also password-protect your hard drive. - Remember to install updates, because they improve phone and application security.
Make sure they are always installed.
Devices
- Watch out for public WiFi networks.
The name of the network may be similar to the place where you are (e.g. "SafeShoppingMallNetwork"), but this does not necessarily mean that it is a network issued by the facility manager. The golden rule is: if you really don't have to, don't use it. It is much better to use a hotspot shared from your smartphone for work or entertainment on the go. - Carefully verify the web addresses of websites that you visit from your device. A correct web address should have the HTTPS protocol, i.e. https://.
- Do not connect accidentally found external drives or other USB storage devices to your computer.
You never know if they are safe or whether they are carrying a virus. It is best to check such media on an old computer without internet connection or at a computer service shop.
Helpful articles See all Helpful articles

Online safety, or what rules should be followed?
The Internet gives its users access to unlimited possibilities - to perform their professional duties remotely, to shop, to learn or to be...

Phishing - what is it and how to defend against it?
One wrong click when using the Internet can be enough to lose sensitive data, including logins and passwords e.g.: for bank accounts. A ph...

Data leakage - what should be done in this situation?
Personal data is confidential information that is used to identify a person's identity. For this reason, they should be duly protected. Ma...

What is two-step verification?
In today's world, cyber security is extremely important. The internet offers many opportunities, but it also carries the risk of data loss...